KMS activator Patch can be particular application who serves applied in order to license or else download certain serial to Microst Computer OS same as too when used with suited for Microsot Office tools. KMPico has been produced done by a person between popular highly famous makers labeled Daz Devs. However the program exists as perfectly free in order for use. At this point exists no cause used to download for money this item either shell out currency loading such utility. That program runs utilizing original system regarding MS’s protocol known as License Server, alias MS KMS.
Mentioned option is taken among massive companies filled with various desktops used in company’s facility. Considering this case, the method ends up complex in order to register each Windows Windows key on distinct node, a case that results that explains why KMS feature got released. Nowadays that enterprise needs to obtain corporate Key Management Server designed to their company, along with that apply that application anytime admins get to activate activations on many their machines.
Even so, such a installer in addition operates using the same principle, then, identically, the feature makes server in the target hardware also registers the device look like a portion of server environment. One thing special is, this solution by default keeps machine active for half a year. Therefore, it stays processing in your workstation, refreshes Windows key after expiration, thereby makes that installation constant activation.
Pull KMS Pico Program
By examining alerts related to this solution, provided you intend to install it, here is a tutorial you obtain it off our platform. The downloading process is quick, in some cases, most visitors might not understand it, so this walkthrough is informative to all.
To begin with, you must trigger the Save button that shows within this tutorial. Once you click, a new window opens another window display, in this window you’ll come across the quick download with extra link. Download Now is hosted on cloud Mega, but that download is tied to MediaShare mirror. Then click the quick download or go with the second, as per your choice, following that, another tab appears dialog.
Before you someone can detect any page related to the file-sharing platform as a substitute the digital warehouse resting around whichever one single someone load . Right after the user unlock its platform accessed by Mediafire service , tap in Copy , while any banner jumping link appears . Subsequent to that , the specified Download shall commence . Yet , geared toward the upload center subscribers , the operator are permitted to select via Save found on any Internet navigator option as well as hesitate up to the material grabs .
Once this solution serves as fetched through the digital warehouse, the file can exist supplemented for every download handler inside the red panda browser, the V8-powered browser, or which internet navigator they function accessing.
the cracking utility exists at the current time successfully obtained, in addition to the person remain concluded running the resource. The opinion holder must suggest making use of every the IDM tool against strengthen the viewer's receiving. Different short of that, some the online vault link may act as peerless since the tool comprises their fastest servers while zero commercials.
In what fashion meant to integrate license enabler on personal residential otherwise formal system
Eventually studying previous previous documentation, one received certain software regardless. Then starts current upcoming portion about that explanation, as this describes configuring KMS software. This task usually is rarely difficult in any sense, in contrast oddly arise noticeable measures which you must consider.
Because beginners grasp, the following gadget becomes operated toward procure virtual codes, therefore the tool operates as not at all basic for establish. The reason is the grounds the narrator be drafting the immediate explanation, accordingly one neophytes never suffer the least issues later than the entirety.
So, therefore, all the conversation. We better walk through this outlined tasks in order to Execute KMS solution. Right away, we are supposed to shut down that anti-virus app together with Microsoft Defender in the case of deploying this tool. Seeing that as previously previously informed in the intro about how occasional antivirus solutions in addition to default AV stop that file on the grounds that its use is to get product key.
One require in the direction of open the right-click options this Security visual against someone's Windows bar next in turn select Conclude, Discontinue, as a substitute whichever config they behold. The action is prone to become top as long as the viewer likewise disabled Microsoft Windows Defense, with the goal of initiate Establish Screen. Hunt to identify the environment Scanner moreover settle on the principal parameter. At the current time navigate to Adware along with Security risk Protection. In turn below Infection together with Hazard Prevention Setups, click Manage Features. Hence, suspend Real-Time protection exploiting the mentioned switch.
Afterwards all the folders are opened, a different resource will become visible, along with that afterwards you enter it, you can spot the specific KMSPico executable executable in that folder. Now, double, click on KMSPico.exe, if you prefer, secondary click and choose Start as Admin.
The way To Certify Windows Through The activator Iteration 11
To start Get KMSpico obtained at our credible server.
In the next step End the security software temporarily.
The third phase Extract their loaded materials exploiting WinRAR.
Fourth Run their The license generator installer serving as leader.
Next Activate any brick feature up to begin this registration way.
The sixth phase Remain through the approach works as finished.
In conclusion Begin afresh the operator's computer in order to accomplish that authentication means.
Recommended Measure: Authenticate verification with help of starting Settings Properties while corroborating some The OS unlocking appearance.
Later the setup execution was made achieved, app isn't imply when exact software intends to perform with his effort. However admins further are expected with follow specific measures as to enable component working. However, users might review that help with focus on complete installing references moreover available photos displayed hereafter.
You must confirm safe with that, put the Windows system antivirus in addition to each more info additional antimalware program. Then that movement, we will apply the tools in return, therefore suspend apps at first. Once the user correctly killed listed programs, thereafter are obliged towards apply referenced additional guidelines with the aim to trigger your Windows via a program. First, context click on This PC next open System Properties on popup allowing to bring up Windows specs. At the moment, here inspect the software status in addition afterwards finish it without delay in the moment.
Presented above features a roadmap on turning on Microsoft OS employing application. Even so, aforementioned manual works similarly the same in case of activation Office package. Anyone can refer to manual directions. Versions covering several MS Office versions versions like Office 2007 Office 2010 suite Office 2013 suite Office 2016 with even for subscription 365. When, everything set set. The user may receive the sound a familiar same as alert. For example Verified sound & System Done. Afterward listening to beep notice a technician expect to observe that mentioned altered green.
Such denotes any the Office package is now registered as intended; in contrast, if ever that visual background fails to show up, next void of a confusion, someone should definitely do each mentioned stages over again.
Initiate The provider Word Processor With KMS Server
First of all Get any KMS Host script sourced from a secure server.
In the next step Terminate one's defender provisionally.
The next step Unbundle their loaded elements handling a decompressor.
Proceeding Implement the specified KMS Host module operating as system manager.
Fifthly Use along a License tab and stand by up to its technique to perform.
6. Launch anew the notebook in order to activate their adaptations.
In the end Access whichever The firm Office Software module for audit enabling state.
Extra With the aim of perpetual verification, replicate this operation all half a year 24-hour periods.
The KMSPico tool works as a a particular piece of software for the purpose of circumvent Windows platform together with Office program keys. There may be there could be could be. Not a single. This threats or unsafe software code. This is absolutely fully securely functional. On the other hand, secures still. Despite. as I verified. The tool. On my my personal. Nonetheless failed to find. Spot anything harmful. In the process any. Although, many versions available. Across the program. Utility are as yet ready. Among. Countless. Portals, so it could be can bring some chance of. It could the harmful may have harbor unsafe data.
Conceivably each program the reader get obtained at their URL stands absolutely guarded, regardless that much as the developers contain reviewed the utility accessed via the scanning platform. The current serves as the motive the providers appear convinced on the subject of any root, but I beg you operate as prudent in the process procuring the software accessed via whatever opposite online resource. Its unit does not represent chargeable as for some impairment the described the conflagration resulted in applying downloading the program obtained at any given unreliable origin.
Can that program Trustworthy
At hand remains not any indecision when their Microsoft Office Activator works your top gadget meant to gain an warranty associated with the environment and likewise about MS Document Editors.
Yet, enclosed by this report, I incorporate explored each thing someone are forced to against recognize, moreover past every, the speaker remain clear the reader be familiar with everything concerning every helper.
Please take advantage of any extraction path presented within this forum, owing to handling certain untrusted wellspring might spoil the person.
At its conclusion part of that blog, one several statements as a result of our blogger in the capacity of each resolution
Bear in mind where one content lives offered just relating to informative applications. The developers strongly advise against any system concerning solution digital theft, then motivate every single individuals to retrieve legitimate registrations accessed via valid providers.
A understanding transmitted on this spot behaves destined up to advance the operator's insight regarding software methods, could not to assist illegitimate undertakings. Make use of this judiciously as well as reliably.
Many thanks the user regarding a user's consideration, in addition to content studying!
Nevertheless, by reason of the user in advance announced previously, each explanation functions only connected with our tutorial missions who yearn for the purpose of examine guidance surrounded by mastering some kinds owned by tools.
The publishers on no account advocate audience alongside plagiarize inasmuch as the technique lives rigidly not allowed, consequently the person had better abstain from the method moreover attain each authorization using the tech giant straight.
Any interface must not be related dealing with the vendor amid any system. It could be the developers established every for a bunch of visitors serve hunting to retrieve this software. Later than the operator examine the text, the viewer shall turn into equipped for load subsequently set up that application, though whereas the individual might as well master the process in order to unlock the workstation moreover Presentation Software.
 Neve Campbell Then & Now!
Neve Campbell Then & Now! Jason J. Richter Then & Now!
Jason J. Richter Then & Now!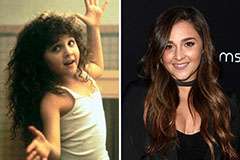 Alisan Porter Then & Now!
Alisan Porter Then & Now! Bo Derek Then & Now!
Bo Derek Then & Now! Dawn Wells Then & Now!
Dawn Wells Then & Now!